COMPUTING RESEARCH HIGHLIGHTS ARCHIVE
An Instant Path to an Online Army
Week: April 19 - April 26, 2013
IT'S been true for a while that if you need to transcribe an audio recording, find contact information for a company, summarize an article, or perform any number of routine tasks, an anonymous online worker can do the job for a small payment. Amazon's Mechanical Turk, for example, recently listed 230,000 available microtasks.
New software could alleviate wireless traffic
 Week: April 12 - April 18, 2013
Week: April 12 - April 18, 2013
The explosive popularity of wireless devices—from WiFi laptops to Bluetooth headsets to ZigBee sensor nodes—is increasingly clogging the airwaves, resulting in dropped calls, wasted bandwidth and botched connections.
Technique Finds Software Bugs in Surgical Robots
 Week: April 4 - April 11, 2013
Week: April 4 - April 11, 2013
Surgical robots could make some types of surgery safer and more effective, but proving that the software controlling these machines works as intended is problematic. Researchers at Carnegie Mellon University and the Johns Hopkins University Applied Physics Laboratory have demonstrated that methods for reliably detecting software bugs and ultimately verifying software safety can be applied successfully to this breed of robot.
Research uses muscle activity to move virtual objects
 Week: March 28 - April 4, 2013
Week: March 28 - April 4, 2013
Today's smartphones and computers offer gestural interfaces where information arrives at users’ fingertips with a swipe of a hand. Still, researchers have found that most technology falls short in making people feel as if they’re interacting with virtual objects the same way they would with real objects.
The Algorithm That Helps You Friend People You Donít Know
 Week: March 8 - March 15, 2013
Week: March 8 - March 15, 2013
Handing over your car keys to a complete stranger is an accepted risk for the benefit of valet parking. But what about handing over access to your inbox for the benefit of increased productivity?
The Algorithm That Helps You Friend People You Donít Know
 Week: March 1 - March 8, 2013
Week: March 1 - March 8, 2013
Detailed analysis of drugs, alcohol & crimes across a city could help target prevention, U-M study finds.
Could a computer on the police beat prevent violence?
 Week: February 21- February 28, 2013
Week: February 21- February 28, 2013
Detailed analysis of drugs, alcohol & crimes across a city could help target prevention, U-M study finds.
New semiconductor research may extend integrated circuit battery life tenfold
 Week: February 1- February 8, 2013
Week: February 1- February 8, 2013
Researchers at Rochester Institute of Technology, international semiconductor consortium SEMATECH and Texas State University have demonstrated that use of new methods and materials for building integrated circuits can reduce power - extending battery life to 10 times longer for mobile applications compared to conventional transistors.
Researchers Find a Better Way to Screen the Tweets
 Week: January 18 - January 25, 2013
Week: January 18 - January 25, 2013
Sifting through social media messages has become a popular way to track when and where flu cases occur, but a key hurdle hampers the process: how to identify flu-infection tweets. Some tweets are posted by people who have been sick with the virus, while others come from folks who are merely talking about the illness. If you are tracking actual flu cases, such conversations about the flu in general can skew the results.
Computer Scientists Measure How Much of the Web is Archived
 Week: January 11 - January 18, 2013
Week: January 11 - January 18, 2013
Twitter’s home page features a regularly updated list of topics that are “trending,” meaning that tweets about them have suddenly exploded in volume. A position on the list is highly coveted as a source of free publicity, but the selection of topics is automatic, based on a proprietary algorithm that factors in both the number of tweets and recent increases in that number.
Computer Scientists Measure How Much of the Web is Archived
 Week: January 4 - January 11, 2013
Week: January 4 - January 11, 2013
Museums and libraries have long attempted to preserve cultural artifacts for future generations. Given that the internet is a cultural phenomenon of extraordinary variety and influence, it's no surprise that archivists are turning their attention to preserving it for future generations.
Small, Portable Sensors Allow Users to Monitor Exposure to Pollution on Their Smart Phones
 Week: December 28 - January 4, 2013
Week: December 28 - January 4, 2013
Computer scientists at the University of California, San Diego have built a small fleet of portable pollution sensors that allow users to monitor air quality in real time on their smart phones. The sensors could be particularly useful to people suffering from chronic conditions, such as asthma, who need to avoid exposure to pollutants.
Researcher Working on Wearable Computers to Monitor Health
 Week: December 14 - December 21, 2012
Week: December 14 - December 21, 2012
Dr. Roozbeh Jafari, assistant professor of electrical engineering at UT Dallas, is developing wearable wireless computers that are about the size of a button. At that size, the system can be easily worn on the body, opening possibilities to improved health monitoring for the elderly and assistance in determining changes in medication dosage needs.
Your next boss could be a computer
 Week: December 7 - December 14, 2012
Week: December 7 - December 14, 2012
Software that delegates tricky problems to human workers is changing the nature of crowdsourcing.
Smartphones Might Soon Develop Emotional Intelligence
 Week: November 29 - December 6, 2012
Week: November 29 - December 6, 2012
If you think having your phone identify the nearest bus stop is cool, wait until it identifies your mood.
Lane-keeping app makes any car smarter
 Week: November 21 - November 28, 2012
Week: November 21 - November 28, 2012
IYou don't have to be rich to get the latest and best in advanced in-car gadgetry. A smartphone app gives any old rust bucket two key safety features you would normally expect to see only in luxury vehicles: a lane-departure warning and driver-fatigue alerts.
Harvard Researchers Use D-Wave Quantum Computer to Fold Proteins
 Week: November 8 - November 16, 2012
Week: November 8 - November 16, 2012
In a paper published in Nature Scientific Reports, http://www.nature.com/srep/index.html, a team of Harvard University researchers, led by Professor Alán Aspuru-Guzik, presented results of the largest protein folding problem solved to date using a quantum computer. The researchers ran instances of a lattice protein folding model, known as the Miyazawa-Jernigan model, on a D-Wave One™ quantum computer.
Researching ways to apply the unique nature of human eye movement to computer technology.
 Week: November 1 - November 8, 2012
Week: November 1 - November 8, 2012
Oleg Komogortsev, assistant professor in the College of Science and Engineering, said eye-movement behavior is unique to every individual and difficult to replicate. Komogortsev's research is based on ocular biometrics, the practice of observing human behavior through the eyes.
Robots using tools: with new grant, researchers aim to create "MacGyver" robot
 Week: October 24 - October 31, 2012
Week: October 24 - October 31, 2012
At a launch event for the school's new wireless technology research center, MIT PhD student Swarun Kumar presented technology for a new autonomo
Driverless car is wireless star at MIT
 Week: October 16 - October 23, 2012
Week: October 16 - October 23, 2012
At a launch event for the school's new wireless technology research center, MIT PhD student Swarun Kumar presented technology for a new autonomous vehicle that recognizes when it may be in danger of striking other cars and pedestrians.
New interactive system detects touch and gestures on any surface
 Week: October 9 - October 16, 2012
Week: October 9 - October 16, 2012
Multitouch surfaces are becoming prevalent, but most existing technologies are only capable of detecting the user's actual points of contact on the surface and not the identity, posture, and handedness of the user. In this paper, we define the concept of extended multitouch interaction as a richer input modality that includes all of this information
App Protects Facebook Users from Hackers
 Week: October 2 - October 9, 2012
Week: October 2 - October 9, 2012
Cyber - crime is expanding to the fertile grounds of social networks and University of California, Riverside engineers are fighting it.
A recent four - month experiment conducted by several UC Riverside engineering professors and graduate students found that the application they created to detect spam and malware posts on Facebook users' walls was highly ac
Researchers Devise More Accurate Method For Predicting Hurricane Activity
 Week: September 26 - October 2, 2012
Week: September 26 - October 2, 2012
The latent behavior of a physical system that can exhibit extreme events such as hurricanes or rainfalls is complex. Recently, a very promising means for studying complex systems has emerged through the concept of complex networks. Networks representing relationships between individual objects usually exhibit community dynamics.
BYU researchers detect fraud with highest accuracy to date
 Week: September 19 - September 26, 2012
Week: September 19 - September 26, 2012
Researchers from Brigham Young University have helped create the most robust and accurate fraud detection system to date using information from publicly available financial statements.
Using business intelligence software that learns and adapts as it processes data, a team of professors from the Marriott School of Management developed a model that correctly detects fraud with 90 percent accuracy.
Automated Worm Sorter Detects Subtle Differences in Tiny Animals Used in Genetic Research
 Week: August 24 - August 31, 2012
Week: August 24 - August 31, 2012
Georgia Tech researchers have demonstrated an automated system that uses artificial intelligence and image-processing technology to rapidly examine large numbers of individual organisms. The researchers used the technology to study Caenorhabditis elegans, a species of nematode widely used in biological research, and found that the system's ability to detect subtle differences from worm-to-worm can identify genetic mutations that might not have been detected otherwise. By enabling thousands of worms to be examined autonomously in a fraction of the time required for conventional manual screening, the technique could change the way that high throughput genetic screening is carried out.
Fighting back against click-spam
 Week: August 16 - August 22, 2012
Week: August 16 - August 22, 2012
University of Texas at Austin researchers recently presented their paper, "Measuring and Fingerprinting Click-Spam in Ad Networks," at the SIGCOMM 2012 conference. The paper aimed to quantify the traffic on an ad network. "To our surprise, we found this was extremely challenging, and, aside from a scattered few anecdotes, there was no well-known, systematic technique, so we decided to come up with one," says University of Texas at Austin's Saikat Guha. The researchers developed a technique that provides the first independent methodology for advertisers to measure the click-spam problem, and supports an automated method for ad networks to identify simultaneous click-spam attacks proactively.
CAVE2: Next-Generation Virtual-Reality and Visualization Hybrid Environment for Immersive Simulation and Information Analysis
 Week: August 2 - August 10, 2012
Week: August 2 - August 10, 2012
This video trailer shows CAVE2 at the University of Illinois at Chicago's Electronic Visualization Laboratory (EVL):
http://youtu.be/d5XDbzy7vuE
At 24-feet wide and covering almost 320 degrees of view, CAVE2 is the largest and highest resolution LCD-based virtual reality system in the world.
EVL invented the original CAVE in 1992 (http://youtu.be/-Sf6bJjwSCE) using cathode ray tube projectors. And it was considered a paradigm shift in virtual reality, moving people away from big heavy VR helmets to light weight LCD shutter glasses.
Graduate student Jon Moeller, ZeroTouch featured in Best Buy commercial
 Week: July 25 - August 3, 2012
Week: July 25 - August 3, 2012
The Texas A&M Interface Ecology Lab introduces the latest generation of the high fidelity ZeroTouch™ Sensor for multi-touch and free-air interaction at the Interactivity exhibition of the ACM CHI human-computer interaction conference (i433 through 5/12/2012). ZeroTouch is a disruptive technology that brings the body into human-centered computing, enabling new forms of expressive, yet precise and powerful interactivity. ZeroTouch turns any display or any area into a multi-touch surface. The latest ZeroTouch sensor's data transfer rate is 8 times faster than before, enabling construction of sensors of any practical size.
Scientists Develop Method for Authenticating Digital Images by Analyzing "Noise"
 Week: July 20 - July 27, 2012
Week: July 20 - July 27, 2012
The past decade has witnessed significant advances in digital image processing and computational photography, resulting in sophisticated image-editing software systems such as Adobe Photoshop and GNU Image Manipulation Program. Yet the ease of digital image manipulation has also posed new challenges, with digital images becoming more vulnerable than their non-digital counterparts to malicious tampering.
RCFile: A Fast and Space-efficient Data Placement Structure in MapReduce-based Warehouse Systems
 Week: July 17 - July 24, 2012
Week: July 17 - July 24, 2012
Industry engineers and academic researchers from Facebook, Ohio State University, and Institute of Computing Technology, Chinese Academy of Sciences have developed a data placement structure, called RCFile, to efficiently store increasingly big data sets using a large and distributed data warehouse. This data placement problem is challenging to big data management and users, such as social network, Web service providers, and online stores.
Microsoft training computers to finish our sentences
 Week: July 5 - July 12, 2012
Week: July 5 - July 12, 2012
A team of computer scientists from Microsoft Research and colleagues from Cornell University and the University of California, Irvine are trying to determine if it is possible for computers to know what humans are going to say before they finish their sentences.
Scientists Build Vascular Network Using Sugar and a 3-D Printer
 Week: June 28 - July 5, 2012
Week: June 28 - July 5, 2012
Keywords: Semantic, Good Turing frequency estimation
Bioengineers have long dreamed of creating living tissue that can be molded into everything from replacement human livers to lab-grown steaks. But a major obstacle has been keeping engineered tissues alive. Cells need a constant supply of nutrients and oxygen, and engineering a blood vessel system to deliver those nutrients and remove waste has remained elusive.
P2P comes to the rescue of Internet video
 Week: June 21 - June 27, 2012
Week: June 21 - June 27, 2012
Keywords: P2p
VTT Technical Research Center of Finland researchers, working with a consortium of 20 industrial partners on the P2P-Next project, have developed NextShare, an open source peer-to-peer (P2P) video-streaming platform.
Jellyfish: Networking Data Centers Randomly
 Week: June 21 - June 27, 2012
Week: June 21 - June 27, 2012
Keywords: Network
While computer network designers have traditionally adhered to carefully planned, symmetrical structures, a team of computer science researchers at the University of Illinois is proposing the exact opposite: complete randomization of the network topology.
Computer Program Spots Fake Product Reviews
 Week: June 15 - June 21, 2012
Week: June 15 - June 21, 2012
Keywords: Artificial Intelligence
A new computer program can spot fake online product reviews by determining whether the distribution of one-star through five-star scores appears natural or not. A graph of an animal population in the wild often has a distinctive shape, with the animalís numbers rising and falling in cycles in response to how many predators there are around or how much food there is to eat.
System Improves Automated Monitoring of Security Cameras
 Week: June 7- June 15, 2012
Week: June 7- June 15, 2012
Keywords: Automated monitoring, security system
Massachusetts Institute of Technology (MIT) researchers have developed a system that can analyze several surveillance cameras more accurately and in less time than it would take a human operator. The system, known as partially observable Markov decision process (POMDP), uses mathematics to reach a compromise between accuracy and speed to enable security staff to act on an intrusion as quickly as possible.
T(ether) - a Spatially- and Body-Aware Window for Collaborative Editing and Animation of 3D Virtual Objects
 Week: June 1- June 7, 2012
Week: June 1- June 7, 2012
Keywords: Architectural design, 3D data
T(ether) is a novel spatially aware display that supports intuitive interaction with volumetric data. The display acts as a window affording users a perspective view of three- dimensional data through tracking of head position and orientation. T(ether) creates a 1:1 mapping between real and virtual coordinate space allowing immersive exploration of the joint domain. Our system creates a shared workspace in which co-located or remote users can collaborate in both the real and virtual worlds.
Totally RAD: Bioengineers create rewritable digital data storage in DNA
 Week: May 25 - May 31, 2012
Week: May 25 - May 31, 2012
Keywords: Bioengeneering, DNA , Recombinase Addressable Data
Stanford University researchers have developed a method to reapply natural enzymes adapted from bacteria to flip specific sequences of DNA back and forth, which can serve as the genetic equivalent of a binary digit. "Essentially, if the DNA section points in one direction, it's a zero. If it points the other way, it's a one," says Stanford graduate student Pakpoom Subsoontorn. "Programmable data storage within the DNA of living cells would seem an incredibly powerful tool for studying cancer, aging, organismal development, and even the natural environment," notes Stanford professor Drew Endy. The method also could form the basis of non-volatile memory.
Bee research breakthrough might lead to artificial vision
 Week: May 11 - May 18, 2012
Week: May 11 - May 18, 2012
Keywords: cognitive tasks
New research reveals that honeybees use multiple rules to solve complex visual problems, and study author Adrian Dyer of RMIT University says the findings help explain how cognitive capacities for viewing complex images evolved in the brain.
Hyperspeed Signaling
 Week: May 4 - May 11, 2012
Week: May 4 - May 11, 2012
Keywords: cyber-security
Imagine if a network administrator had powers like the superhero Flash-perceived invisibility, omnipresence and superior surveillance and reconnaissance abilities-that would enable the administrator to send early warnings of threats and trigger mitigation efforts before malicious traffic reaches its target.
Living in the Livehood
 Week: April 27 - May 4, 2012
Week: April 27 - May 4, 2012
Keywords: social engineering, social media, datamining
Carnegie Mellon researchers believe they can capture the essence of an area based on what Foursquare users do there.. The Livehoods Project presents a new methodology for studying the dynamics, structure, and character of a city on a large scale using social media and machine learning.
Data Furnace
 Week: April 13 - April 20, 2012
Week: April 13 - April 20, 2012
Keywords: data centers, sustainability
In a paper presented this year at the Usenix Workshop on Hot Topics in Cloud Computing, two researchers at the University of Virginia and four at Microsoft Research explored how micro data centers could be placed inside homes and used as a source of heat. The authors call the concept the "data furnace."
Financial Modeling with Twitter
 Week: March 30 - April 7, 2012
Week: March 30 - April 7, 2012
Keywords: financial modeling, computation, twitter
University of California, Riverside researchers have developed a model that uses Twitter data to help predict the traded volume and value of a stock the following day. The model, developed by Riverside professor Vagelis Hristidis, outperformed other baseline strategies by as much as 11 percent, and did better than the Dow Jones Industrial Average during a four-month simulation.
SafeSlinger
 Week: March 23-30, 2012
Week: March 23-30, 2012
Keywords: security, communications, encryption
Researchers at Carnegie Mellon University's CyLab developed SafeSlinger to enable users to safely and securely exchange messages. SafeSlinger makes sending secure messages easy. Just keep your passphrase a secret, and only you and the other party can read messages. Messages cannot be read by your cellular carrier, Internet-provider, employer, or anyone else.
Lie To This
 Week: March 16-23, 2012
Week: March 16-23, 2012
Keywords: hci
Researchers at the University at Buffalo, The State University of New York, have developed software that claims to be able to analyze eye movement successfully to identify whether or not
a subject is lying to it - with 82.5 percent accuracy. The researchers, presented their results at the 2011 IEEE International Conference on Automatic Face and Gesture Recognition a year ago.
Raspberry Pi
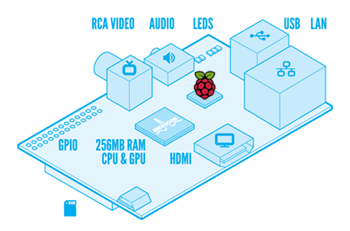 Week: March 9-16, 2012
Week: March 9-16, 2012
Keywords: hardware
The $25 Raspberry Pi computer could have an impact far beyond the educational sector, with early production runs showing significant demand for the technology. The credit card-sized Raspberry Pi is a fully functional Linux computer, complete with Ethernet and USB ports and HDMI output. To use it, people need to plug in a keyboard and attach the device to a TV. The device was created by the Raspberry Pi Foundation, which wants to improve computer science education by making an affordable, flexible platform available to budding programmers.
Dark Web Project
 Week: March 2-9, 2012
Week: March 2-9, 2012
Keywords: Social Media, algorithms
Researchers engaged in the "Dark Web Project," a program started partly in response to the 9/11 terrorist attacks, have developed methods for tracking the spread of dangerous ideas through certain rogue and jihadi Web forums. Using a mathematical model known as SIR, used by epidemiologists to describe the transmission of disease, researchers have determined that the infection rate for becoming a suicide bomber is 2 in 10,000, Hsinchun Chen of the University of Arizona in Tucson reported February 18 at the annual meeting of the American Association for the Advancement of Science.
Seriously Rapid Source Review
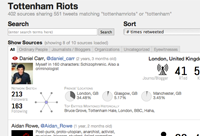 Week: Feb 25 - March 2, 2012
Week: Feb 25 - March 2, 2012
Keywords: Social Media, algorithms
Researchers at Rutgers University and Microsoft developed Seriously Rapid Source Review to give journalists access to breaking news like never before. Reporters won't have to comb the web or Twitter's 200 million tweets a day for sources. This program (under development) will act like a sieve that pull tweets from key sources currently sharing reports, images and video from the ground.
Forecasting Popularity
 Week: Feb 10 - 17 , 2012
Week: Feb 10 - 17 , 2012
Keywords: Social Media, algorithms
Bernardo Huberman and colleagues at Hewlett-Packard's Social Computing Lab have developed an algorithm that can predict how popular new stories will become. Journalists rely on their gut feeling and their understanding of the dynamics of their audience when they choose to write about topics, but the algorithm could automate this process.
Graphene, It's Cool
 Week: Feb 3 - 10 , 2012
Week: Feb 3 - 10 , 2012
Keywords: nano-devices, material sciences
Researchers at the University of California, Riverside (UCR), the University of Texas at Austin, the University of Texas at Dallas, and Xiamen University have shown that the thermal properties of isotopically engineered graphene are better than those of graphene in its natural state. The results mean that graphene is one step closer to being used as a thermal conductor for managing heat dissipation in electronic devices.
Kiwi's Software Wows Google, NASA
 Week: Jan 20 - 27 , 2012
Week: Jan 20 - 27 , 2012
Keywords: clusters, gpl, parallel processing
New software used worldwide to connect multiple screens to form one big image is the work of a New Zealand student. The University of Waikato's Paul Hunkin developed ClusterGL in 2008 for use with Waikato's display wall as a side project.
A Smart Phone That Knows You're Angry
 Week: Jan 13 - 20, 2012
Week: Jan 13 - 20, 2012
Keywords: smartphone, sensors, emotion recognition
Samsung has developed a prototype emotion detection system for smartphones. Rather than use specialized sensors or cameras, the system monitors certain inputs, such as the speed at which a user types, how often the backspace or special symbol buttons are pressed, and how much the smartphone shakes. Normal cell phone use enables the system to postulate the emotional state of the user, says Samsung researcher Hosub Lee.
Naval Researchers Pioneer TCP-Based Spam Detection
 Week: Jan 6 - 13, 2012
Week: Jan 6 - 13, 2012
Keywords: TCP/IP, spam
U.S. Naval Academy researchers have developed a method for analyzing email traffic in real time to identify spam messages as they come across the wire, using the information from the Transmission Control Protocol (TCP) packets that carry the messages. Experts say the technique could be a good spam-fighting method because it does not require the content of the email to be scanned.
Computers Implanted in Brain Could Help Paralyzed
 Week: December 23 - 30, 2011
Week: December 23 - 30, 2011
Keywords: image analysis, computer vision, photoshop, human perception
The University of California (UC), Berkeley and UC San Francisco launched the Center for Neural Engineering and Prostheses a year ago to take advantage of the neurology expertise in San Francisco and the engineering skills in the Bay Area. The center develops technologies that enable the human brain to control electronic devices.
Photoshopped?
 Week: December 16 - 23, 2011
Week: December 16 - 23, 2011
Keywords: image analysis, computer vision, photoshop, human perception
Dartmouth College researchers have developed software that measures how much fashion and beauty photographs have been altered. The researchers, led by Dartmouth professor Hany Farid and Ph.D. student Eric Kee, say the new tool could be a technological step to address concerns about the prevalence of digitally edited images in advertising and fashion magazines.
Identifying Similar Images Across Domains
 Week: December 2 - 9, 2011
Week: December 2 - 9, 2011
Keywords: image matching, visual similarity, saliency, image retrieval, painting, sketches
Computers can mimic the human ability to find visually similar images, such as photographs of a fountain in summer and in winter, or a photograph and a painting of the same cathedral, by using a technique that analyzes the uniqueness of images, say researchers at Carnegie Mellon University's School of Computer Science.
New Photonics-Based Access Methods for Main Memory Systems
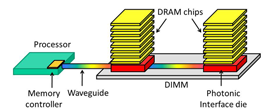 Week: November 11 - 18, 2011
Week: November 11 - 18, 2011
Keywords: Memory systems, Silicon photonics, 3D stacking, Memory access protocol
Multi-core processors demand large amounts of data. Typically, this data is provided by the memory system via electrical pins on a processor package. Unfortunately, the growth in data demands is out-pacing the growth in the number and speed of pins on a package.
Unlocking The Key To Human Intelligence
 Week: October 28 - November 4, 2011
Week: October 28 - November 4, 2011
Keywords: CSAIL, artificial intelligence
What if machines could think like us - comprehending social cues, visual prompts and spoken words just like a human would? For CSAIL Professor Patrick Winston, the Ford Professor of Artificial Intelligence and Computer Science and leader of the Genesis Group at CSAIL, uncovering the true nature of human intelligence is the next grand challenge.
How the Internet Architecture Got it's Hourglass Shape
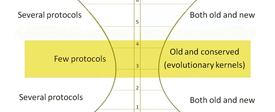 Week: October 14-21, 2011
Week: October 14-21, 2011
Keywords: Internet Architecture, Future Internet, Layering, Network Science, Evolutionary Kernels, Evolution
The Internet protocol stack has a layered architecture that resembles an hourglass. The lower and higher layers tend to see frequent innovations, while the protocols at the waist of the hourglass appear to be "ossified".
Airshark: Detecting Non-WiFi RF Devices using Commodity WiFi Hardware
 Week: September 30 - October 7, 2011
Week: September 30 - October 7, 2011
Keywords: computer networks, wifi, intrusion detection
University of Wisconsin, Madison researchers have developed Airshark, software that enables wireless access points to automatically detect radio-frequency interference and make adjustments to preserve the quality of Wi-Fi connections. They say the software could eliminate the need for separate spectrum analyzers that discover interfering devices but do nothing to counter the interference.
Football: A coach for AI
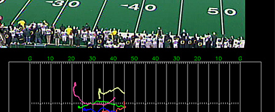 Week: September 16 - 23, 2011
Week: September 16 - 23, 2011
Keywords: Artificial intelligence, Automatic knowledge transfer
OSU researchers in artificial intelligence have made an important advance that blends computer vision, machine learning and automated planning, and created a new system that may improve everything from factory efficiency to airport operation or nursing care.
Debugging Supercomputers
Week: August 19 - 26, 2011
 Keywords: debugging, supercomputers, parallel processing
Keywords: debugging, supercomputers, parallel processing
When scientific applications run on extreme-scale systems, a single fault that disables a small portion of the application can bring the entire execution to a sudden halt, costing machine and programmer time. The Stack Trace Analysis Tool (STAT) developed by Lawrence Livermore National Laboratory, Livermore, Calif., the University of Wisconsin, Madison, and the University of New Mexico, Albuquerque is designed to help developers prevent these small faults from hindering valuable research.
Detecting Diseases With Computers
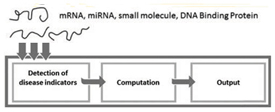 Week: August 12 - 19, 2011
Week: August 12 - 19, 2011
Keywords: nanocomputing, disease, medical
Wouldn't it be nice if your computer knew you were sick before you yourself knew? Ehud Shapiro and coauthors from the Weizmann Institute of Science in Rehovot, Israel have made a bimolecular computer that can detect many types of molecules autonomously. It theoretically could lead to nano-sized computers that would detect disease in your body far before you could know you were sick.
Humanized Robots Explore Human Sexuality
Week: August 5 - 12, 2011
Keywords: language translation, parsing, graphics, visualization, writing, education
A computerized human nervous system function emulator (HNSFE) has been expanded to include elements of courtship, pair bonding, erotic stimulation and sexual intercourse, producing a human sexual function emulator (HSFE). The HNSFE is a biologically-inspired, open systems, multitasking, multiprocessor, IEEE 1275 program which imitates many neural-cognitive operations of the human brain. It is the control element of the author's robotic "Android with Neural Network, Intellect and Emotions" (ANNIE).
Write it, See it: Visualizing History
 Week: July 22 - 29, 2011
Week: July 22 - 29, 2011
Keywords: language translation, parsing, graphics, visualization, writing, education
Helping students transform mundane text into visuals can improve attention and speed learning. A team of computer scientists and education researchers worked to generate a system that produces 3D scenes from written language. The system, called WordsEye, analyzes text, including handling complex context based description, such as relational words, and then refers to a 3D object library to output a visual.
Using Handwriting Styles to Understand Historic Documents
 Week: July 15 - 23, 2011
Week: July 15 - 23, 2011
Keywords: handwriting, OCR, digital libraries, text recognition
The best text recognition tools struggle to reliably identify text in handwritten documents. By analyzing handwriting styles, Dr. Venu Govindaraju is working to improve the performance for digitizing text in handwritten documents. At the same time, his techniques could enable forensic analysis of handwriting to determine the author of documents whose writers are still unknown. Unlike other forms of optical character recognition, Dr. Govindaraju's technique doesn't rely on context or grammar rules, it can apply to all languages.
Health Care of the Future
 Week: July 8 - 15, 2011
Week: July 8 - 15, 2011
Keywords: CSAIL, MIT, computer science, natural language processing, medical engineering
The Clinical Decision Making Group at MIT's Computer Science and Artificial Intelligence Laboratory, led by Professor Peter Szolovits, is dedicated to using natural language processing techniques to make better sense of unstructured medical records.
BinCam - Waste logging for Behavioral Change
 Week: June 24 - July 1, 2011
Week: June 24 - July 1, 2011
Keywords: HCI, Social Computing
BinCam is a two-part personal informatics system designed to increase individuals's awareness of their food waste and recycling behaviour. It uses a standard kitchen bin augmented with a mobile phone to automatically capture and log an individual's waste management activity. Photos are tagged using Amazon Mechanical Turk and uploaded to the BinCam application on Facebook, which encourages playful engagement and reflection upon a user's personal bin data. People can review and share communications about the bin-related behaviour of themselves and others.
Digital Anty-bodies take on Viruses
 Week: June 10 - 17, 2011
Week: June 10 - 17, 2011
Keywords: Distributed Sensor Networks
Professor of Computer Science Errin Fulp is training an army of "digital ants" to turn loose into the power grid to seek out computer viruses trying to wreak havoc on the system.
MobiCon: Next Generation Mobile and Ubiquitous Platforms
![]() Week: May 13 - 20, 2011
Week: May 13 - 20, 2011
Keywords: Distributed Sensor Networks
The main insight behind MobiCon is that instead of sensing all the sensors all the time, the system determines the sensors that are required by the union of applications that are currently active.
Hive Security
Week: May 6-13, 2011
Keywords: botnets, cybersecurity
The Department of Homeland Security has published an interesting paper that explores a novel approach to combat threats from botnets and their ilk. It involves a network of machines collaborating to stave off attacks.
Passwords that are Harder to Hack
Week: April 29 - May 6, 2011
Keywords: compiler, correctness, c programming language
Researchers from the Max-Planck-Institut fur Physik komplexer Systeme and from Axioma Research have devised a new method to create passwords that are harder to hack, but easier to remember.
Killing Compiler Bugs
Week: April 22 - 29, 2011
Keywords: compiler, correctness, c programming language
Compilers are software tools that translate programs in a high-level language into binary code that machines can directly execute. Bugs in compilers for the C language can undermine the correctness of operating systems, financial systems, controllers embedded in cars or medical equipment, and other important systems. Computer scientists at the University of Utah have developed a technique for automatically locating bugs in C compilers and have used it to find 350 previously-unknown flaws, most of which have already been fixed by compiler developers.
CSAIL Researcher Creates Customizable Buttons
Week: April 15 - 22, 2011
Keywords: Robotics, Kinect, ROS
If you need a little dose of magic in your life look no further than a new interface developed by Garratt Gallagher. Using a Microsoft Kinect video game system in conjunction with ROS (open-source Robot Operating Software developed by Willow Garage), Gallagher, a Systems Robotics Engineer at MIT's Computer Science and Artificial Intelligence Laboratory, has created Customizable Buttons.
Computer Based Diabetic Retinopathy Screening
Week: March 18 - March 24, 2011
Keywords: retinopathy, algorithms
Diabetic retinopathy (DR) is a complication resulting from the diabetes. According to the National Eye Institute estimation 40-45% of the diabetics suffer from certain level of diabetic retinopathy. The estimated incidence rate of DR is 30% and 80% respectively for diabetics with 5 and 15 years of history. DR is classified into two categories, four stages: (Mild, moderate and severe) non-proliferative retinopathy, and profilerative retinopathy. Early detection of DR allows timely therapeutic treatments to slow down the DR development.
Extending the Reach of the White Cane for Blind Wheelchair Users
Week: March 11 - March 18, 2011
Keywords: Computer Architectures, Algorithms, Security
Modern networks need to be constantly on the prowl for the bad guys: worms, intruders, denial-of-service attacks, etc. As we learn more information about the way these bad guys attack our machines we can start to develop rules - or specifically sequences of text - that tell us that an attack is occurring. The problem is that this list of rules already has more than 100,000 entries, and is growing larger by the second. While that does not sound too bad, the problem is that we want to search every byte of every pieces of data sent over the internet for each and every instance of these 100,000 rules - many billions of characters of text each and every second.
Extending the Reach of the White Cane for Blind Wheelchair Users
Week: March 4 - March 11, 2011
Keywords: Human computer interaction, Computer Vision
Approximately one in ten blind persons uses a wheelchair, and independent travel is extremely difficult for this population. With funding from the NSF, the Smith-Kettlewell Eye Research Institute has developed a prototype computer vision system at that allows a visually impaired wheelchair rider to "interrogate" the environment using a standard white cane to detect important terrain features such as obstacles and curbs. This system allows the user to interrogate the environment by sweeping a standard (unmodified) white cane (which a visually impaired rider is already likely to be using) back and forth, from left to right. Using a pair of video cameras mounted on the wheelchair facing the path ahead, the system continuously tracks the cane location and sounds an audio alert if a terrain feature is detected in the direction the cane is pointing. Thus, the user interface extends the reach of the white cane in a seamless and intuitive way while permitting normal use of the cane.
CSAIL Zooms In With Computational Photography
Week: February 28 - March 1, 2011
Keywords: Fault Tolerance
MIT Computer Science and Artificial Intelligence Lab (CSAIL) Professors Bill Freeman and Frèdo Durand are currently devoting their efforts to making photography a more precise and accessible art form, one where widespread errors such as blur are but a distant memory. Computational photography, a means of expanding the capabilities of and tackling common problems in photography through algorithms, will be for the camera what the iPhone has been to the mobile phone market, according to Durand and Freeman.
Zero-Cost Self-Repair of Microprocessors
Week: February 11 - 18, 2011
Keywords: Fault Tolerance
Professor Sorin and his team at Duke University have developed a hardware-free scheme, called Detouring, for tolerating permanent faults in microprocessors. Most prior self-repair schemes use significant amounts of redundant hardware, and a fault in one unit can be tolerated by using another unit of the same kind.
Exploration of Distributed Creativity in Multi-Site 3D Tele-Immersive
 Week: February 4 - 11, 2011
Week: February 4 - 11, 2011
Keywords: 3D imaging, teleconferencing
This project develops teleimmersive technology which enables users to collaborate remotely and experience the benefits of a face-to-face meeting in a virtual environment. Using a multi-camera setup, the immersive technology creates an accurate, full-body 3D reconstruction in real time, which is sent through the network to the remote location. Geographically distributed teleimmersion users can meet in a virtual space which can also include different synthetic objects or data that the users wish to interact with.
Fruit Fly Suggests New Solution to Computer Networking Problem
 Week: January 21 - 28, 2011
Week: January 21 - 28, 2011
Keywords: distributed computing, networking, maximal independent set
The fruit fly has evolved a method for arranging the tiny, hair-like structures it uses to feel and hear the world that's so efficient a team of U.S. and Israeli scientists says it could be used for distributed computing applications.
Personalized Assistive Human-Robot Interaction for Socially-Assistive Post-Stroke Rehabilitation
Week: January 14 - 21, 2011
Keywords: Stroke Detection, Robotics, Human-robot interaction
An interdisciplinary project has developed an approach that uses a friendly robot and wearable sensors to monitor, coach, and assist people suffering from stroke. Principal Investigators Maja Mataric and Carolee Winstein of the University of Southern California have brought together expertise in the areas of assistive human-robot interaction, stroke diagnosis, and rehabilitation in an interdisciplinary project that is developing a novel technology based on a socially assistive robot SAR as the personalized rehabilitation coach.
Breaking the O(n^2) Bit Barrier
Week: January 7 - 14, 2011
Keywords: Scalable Byzantine Agreement
The paper "Breaking the O(n^2) Bit Barrier: Scalable Byzantine Agreement with an Adaptive Adversary" by Valerie King, of the University of Victoria BC, and Jared Saia, of the University of New Mexico, recently received the best paper award at the prestigious Principles of Distributed Computing (PODC) conference. This paper describes an algorithm that solves the Byzantine agreement problem with significantly less communication than any previous results. The venerable Byzantine agreement problem addresses the question of how we can create a reliable system out of unreliable components. In particular, it requires a set of processors to come to agreement on a single bit, even when there is no trusted external party, and, moreover, a hidden fraction of the processors are controlled by an adversary.
Making a Smarter Power Grid
 Week: November 26 - December 3, 2010
Week: November 26 - December 3, 2010
Keywords: Smart grid, machine learning, Columbia
The DOE awarded Consolidated Edison Company of New York (ConEdison) $45 million for its Secure Interoperable Open Smart Grid Demonstration Project - one of the ARRA Smart Grid Demonstration Projects selected nationwide. As ConEdison's long time collaborator in R&D, Columbia University's Center for Computational Learning Systems (CCLS), led by director Dr. David L. Waltz, is working with ConEdison in making a smarter power grid that has the potential to not only eliminate the blackouts New York City residents endured and support emerging smarter technologies such as electric vehicles but also influence the way engineering is taught.
Speedy Algorithm for Linear Systems
 Week: November 19 - 23, 2010
Week: November 19 - 23, 2010
Keywords: SDD systems, symmetric diagonally dominant systems, linear systems, spectral graph theory
Computer scientists at Carnegie Mellon University have devised an innovative and elegantly concise algorithm that can efficiently solve systems of linear equations that are critical to such important computer applications as image processing, logistics and scheduling problems, and recommendation systems.
Low Cost Mobile Ultrasound
 Week: November 12 - 19, 2010
Week: November 12 - 19, 2010
Keywords: Health and Medicine, Ultrasound, Health IT
The UW device consists of an ultrasound Interson probe that connects via a USB port to a netbook with a touch-sensitive screen. It is designed to be cheap, portable, durable and easy to use and utilize existing local healthcare resources in order to create a sustainable solution that does not depend on continuous foreign assistance.
Cancer or Anthrax Detection in Moments
 Week: November 7 - 12, 2010
Week: November 7 - 12, 2010
Keywords: Biomolecules, cancer detection, anthrax detection, "Lab on a chip", Mohseni, cancer antigens
Four EECS graduate students at NU have created a new chip-sized sensor that will make it easier to detect dangerous substances in patients. The sensor, 3mm in length, uses a laser and an antenna to identify and catalogue low-concentration biomolecules, such as cancer antigens or anthrax spores.
Supercomputers Identify Supercell Storms and Tornadoes
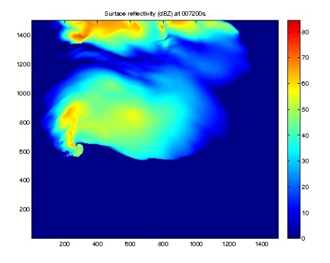 Week: October 7 - 14, 2010
Week: October 7 - 14, 2010
Keywords: Data Mining, Environment
After a long winter, many people look forward to spring. However, in the Midwest, spring also brings tornado season. The very word tornado is enough to scare some people, especially those who have personally experienced one of these violent storms. Others, including researchers at the University of Oklahoma, see tornadoes as a puzzle to be solved. Dr. Amy McGovern at the University of Oklahoma in Norman Oklahoma, studies tornadoes using advanced data mining techniques.
Next Generation Automatic Memory Management
 Week: Sep 3 - 10, 2010
Week: Sep 3 - 10, 2010
Keywords: Memory Management, Garbage Collection, Algorithms
Modern object-oriented programming languages such as Java, JavaScript, Ruby, and C# are becoming ubiquitous. A primary reason for this trend is that these languages provide automatic memory management (garbage collection), which relieves programmers of the burden of explicitly freeing memory that is no longer needed. Professor Kathryn McKinley at the University of Texas at Austin has led an NSF-funded research project, in collaboration with Steve Blackburn at the Australian National University, that is exploring how to build the software infrastructure that executes managed programs, i.e., programs in languages that provide automatic memory management. Garbage collection provides a number of software engineering benefits such as preventing common programmer memory errors that are among the most difficult to diagnose and fix. However, in the past, programs in garbage collected languages tended to be slower.
Sign Language by Cell Phone
 Week: August 20 - 27, 2010
Week: August 20 - 27, 2010
Keywords: MobileASL, ASL, video compression
MobileASL is a video compression project at the University of Washington with the goal of making wireless cell phone communication through sign language a reality in the U.S.
Gamers Beat Algorithms at Protein Folding
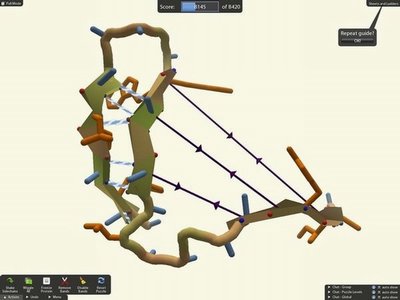 Week: August 6 - 13, 2010
Week: August 6 - 13, 2010
Keywords: gene folding, crowd sourcing, algorithms, pattern recognition
People exert large amounts of problem-solving effort playing computer games. Simple image- and text-recognition tasks have been successfully "crowd-sourced" through games, but it is not clear if more complex scientific problems can be solved with human-directed computing. Protein structure prediction is one such problem: locating the biologically relevant native conformation of a protein is a formidable computational challenge given the very large size of the search space.
Programming Visually with Sikuli
 Week: June 3 - 10, 2010
Week: June 3 - 10, 2010
Keywords: Sikuli, GUI, programming, MIT, Computer Science and Artificial Intelligence Lab, Rob Miller, computer vision
The latest from the User Interface Design Group at MIT's Computer Science and Artificial Intelligence Laboratory, it's a programming tool that has the ability to see like a human being. Not only does it put the graphical user interface (or GUI) in the hands of programmers, but it may one day put programming in the hands of everyday computer users.
PhotoCity: Modeling the World from Photographs
 Week: May 13 - 20, 2010
Week: May 13 - 20, 2010
Keywords: Photosynth, digital photography, computer vision
First there was Photosynth, a collaboration between the University of Washington and Microsoft that constructs 3D models of points of interest from hundreds of tourist photos, allowing those photos to be "navigated" in 3D space. Now there is PhotoCity, a collaboration between the University of Washington and Cornell University that hopes to construct 3D models of entire cities and university campuses from hundreds of thousands or millions of photographs.
Skin As Input For Smart Phones and Mobile Devices
 Week: April 23 - 30, 2010
Week: April 23 - 30, 2010
Keywords: skinput, cmu, keypads, touchscreens, body input
A combination of simple bio-acoustic sensors and some sophisticated machine learning makes it possible for people to use their fingers or forearms - potentially, any part of their bodies - as touchpads to control smart phones or other mobile devices.
Re-Inventing the Graphical User Interface
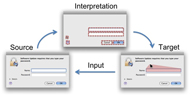 Week: March 31 - April 9, 2010
Week: March 31 - April 9, 2010
Keywords: Graphical User Interface, GUI, Prefab, widget, toolkit
The Prefab system, designed by University of Washington researchers James Fogarty and Morgan Dixon, allows users to customize the graphical user interfaces of applications without access to the application or GUI toolkit source code.
"One Keypad per Child" Lets School Children Share Screen to Learn Math
 Week: January 14 - 21, 2010
Week: January 14 - 21, 2010
Keywords: educational technology, information technology for development, University of Washington
University of Washington computer science undergraduates have developed a system that lets up to four students share a single computer to do interactive math problems. Early tests show that students using the tool are able to share a single screen while working on problems at their own pace, effectively quadrupling the number of computers available for math exercises.
New Search Technique for Images and Videos
 Week: November 13 - November 20, 2009
Week: November 13 - November 20, 2009
Keywords: object detection, action recognition, UCSC
Engineers at the University of California, Santa Cruz, have developed a powerful new approach to a fundamental problem in computer vision: how to program a computer to recognize or categorize what it "sees" in an image or video. Their software could change the way people search the Web for photos and videos, and it may have applications in many other areas as well, such as video surveillance and security systems.
Open Data Kit: Cell Phones Become Handheld Tools for Global Development
 Week: October 30 - November 6, 2009
Week: October 30 - November 6, 2009
Keywords: technology for development, developing world, Android, Google, data collection, University of Washington
Computer scientists at the University of Washington have used Android, the open-source mobile operating system championed by Google, to turn a cell phone into a versatile data collection device. Organizations that want a fully customizable way to, say, snap pictures of a deforested area, add the location coordinates and instantly submit that information to a global environmental database now have a flexible and free way to do it.
Rome Was Built in a Day, with Hundreds of Thousands of Digital Photos
 Week: October 1 - 8, 2009
Week: October 1 - 8, 2009
Keywords: computer graphics, computer vision, computational photography, 3D reconstruction, Photosynth
Several years ago, a collaboration between computer graphics and computer vision researchers at the University of Washington and Microsoft yielded Photosynth (http://photosynth.net/), a revolution in organizing and navigating digital photographs. Now, that same collaboration has yielded "Rome In A Day," which reconstructs entire cities from images harvested from the web, in less than a day of computation time per city.
Cornell Computer Scientists Track the News Cycle
![]() Week: August 14 - 21, 2009
Week: August 14 - 21, 2009
Keywords: Data-mining, Media, News-tracking, Memes
Cornell computer scientists have mapped the way stories rise and fall in popularity over time. As more and more information becomes available online, it is possible to track the life cycle of a particular news story.
Vanish: A Tool to Make Online Personal Data Self-Destruct
 Week: July 24 - 31, 2009
Week: July 24 - 31, 2009
Keywords: Internet, security, privacy, P2P, encryption, cryptography, distributed hash tables
Vanish is a research system designed to give users control over the lifetime of personal data stored on the web or in the cloud. Specifically, all copies of Vanish encrypted data - even archived or cached copies - will become permanently unreadable at a specific time, without any action on the part of the user or any third party or centralized service.
Kidney Exchange Algorithm Launches Chain of 10 Transplants
 Week: July 17 - 24, 2009
Week: July 17 - 24, 2009
Keywords:Kidney exchange, kidney donation, organ donation, live donation, live organ donation, kidney paired exchange, matching algorithm, clearing algorithm, exchange clearing, CMU, Carnegie Mellon University, Tuomas Sandholm, United Network for Organ Sharing, UNOS, New England Journal of Medicine
An algorithm devised by Carnegie Mellon computer scientists launched a long-running chain of live kidney donations that thus far has resulted in 10 patients receiving kidney transplants, with the potential for even more.
IBM Claims Cryptographic Cloud Security Challenge Solved
 Week: July 3 - 10, 2009
Week: July 3 - 10, 2009
Keywords: Cryptography, Cloud Computing Security
Stanford Ph.D. student and IBM researcher Craig Gentry may have taken a big step forward in the solving the problem of data security in cloud computing. In his recently released paper, "Fully homomorphic encryption using ideal lattices", Gentry describes a method which allows processing of encrypted data without knowing its content.
Machine Learning Applied to Indus Script
 Week: May 15 - 22, 2009
Week: May 15 - 22, 2009
Keywords: machine learning, linguistics, India, ancient languages
The Rosetta Stone allowed 19th century scholars to translate symbols left by an ancient civilization and thus decipher the meaning of Egyptian hieroglyphics. But the symbols found on many other ancient artifacts remain a mystery, including those of a people that inhabited the Indus valley on the present-day border between Pakistan and India. Some experts question whether the symbols represent a language at all, or are merely pictograms that bear no relation to the language spoken by their creators.
Robots that Take Orders From the Brain
 Week: April 17 - 24, 2009
Week: April 17 - 24, 2009
Keywords: neurobotics; prosthetics; disabilities; artificial hand; brain-computer interface
At the University of Washington, MacArthur "genius" award-winner Yoky Matsuoka is leading an effort to build robotic hands and other devices that will take commands directly from the human brain — and revolutionizing the opportunities for people with disabilities to function more fully.
Brown Scientists Build Robot That Responds to Human Gestures
 Week: April 10 - 17, 2009
Week: April 10 - 17, 2009
Keywords: Robotics, Human-Robot Interaction
Brown University researchers have demonstrated how a robot can follow human gestures in a variety of environments — indoors and outside — without having to adjust for variations in lighting. The achievement is an important step forward in the quest to build fully autonomous robots as partners for human endeavors.
Epidemiologic Model Shows Potential for Wireless Infection Spread and Prevention
Week: Feb 26 - Mar 6, 2009
Keywords: Malware, wifi, indiana university, school of informatics, epidemiology, steve myers, alex vespignani
 Can a focus on epidemiology help create safer networks? Researchers at Indiana University have created a model based on principles of infectious disease to study how malware might spread through a WiFi network. Indiana University professors Steven Myers and Alex Vespignani, and collaborators Vittoria Colizza and Hao Hu, modeled that the spread of malware on common WiFi networks much as an epidemiologist would model the spread of disease in a population and determined that large “epidemics” of malware can be effectively halted by bringing encryption rates on networks to a given threshold value.
Can a focus on epidemiology help create safer networks? Researchers at Indiana University have created a model based on principles of infectious disease to study how malware might spread through a WiFi network. Indiana University professors Steven Myers and Alex Vespignani, and collaborators Vittoria Colizza and Hao Hu, modeled that the spread of malware on common WiFi networks much as an epidemiologist would model the spread of disease in a population and determined that large “epidemics” of malware can be effectively halted by bringing encryption rates on networks to a given threshold value.
MIT's Sixth Sense
Week: Feb 5-12, 2009
Keywords: interfaces, just-in-time-information, mobile, tangible, ubiquitous
The Fluid Interfaces research group at MIT has developed a wearable, ultra-portable personal computer. This combination of a webcam, smartphone and a battery powered pico projector can turn any surface into a gesture-controlled touch screen.
Cell Phones with Sensors aid Fitness, Environmental Awareness
Week: Dec 18-25, 2008
Keywords: cell phone, ubiquitous computing, ubiquitous sensing, activity inference
Researchers at the University of Washington and Intel have created two new cell phone applications, dubbed UbiFit and UbiGreen, to automatically track workouts and green transportation. The programs display motivational pictures on the phone's background screen that change the more the user works out or uses eco-friendly means of transportation.
Brown University's Michael Black and Alexandru Balan Create Program To Calculate Body Shape
Week: Dec 11-18, 2008
Keywords: 3-D model, body shape, vision, Michael Black, Brown University, laser scans
Imagine you are a police detective trying to identify a suspect wearing a trench coat, baggy pants and a baseball cap pulled low. Or imagine you are a fashion industry executive who wants to market virtual clothing that customers of all shapes and sizes can try online before they purchase. The main obstacle to these and other pursuits is creating a realistic, 3-D body shape - especially when the figure is clothed or obscured.
Zoetrope Searches the Historical Web
Week: Dec 4-11, 2008
Keywords: historical Web search, university of washington
University of Washington Computer Science & Engineering Ph.D. student Eytan Adar and his colleagues at UW and Adobe Systems are grabbing hold and storing historical sites that users can easily search using an intuitive application called Zoetrope. (The Internet Archive has been capturing old versions of Web sites for years, but there is no easy and flexible way to search the archive.)
Algorithm Estimates Geographic Location of Photos
Week: Nov 19-26, 2008
Keywords: Big-Data, Internet, GPS, geolocate, image, im2gps
Researchers at Carnegie Mellon University have devised the first computerized method that can analyze a single photograph and determine where in the world the image likely was taken. It's a feat made possible by searching through millions of GPS-tagged images in the Flickr online photo collection.
Turning 2D Images into 3D Models
Week: Nov 12-19, 2008
Keywords: image, 3D model, algorithm model, artificial intelligence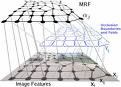
Many artists spend their lives trying to render three-dimensional reality into a realistic two-dimensional image. Make3D does the opposite: it takes a two-dimensional image and digitally creates a three-dimensional model to give the viewer multiple perspectives of the same image.
New Algorithm Significantly Boosts Routing Efficiency of Networks
Week: Oct 24-31, 2008
Keywords: Networks, routing, algorithms
A new algorithm developed by computer scientists from UC San Diego's Jacobs School of Engineering helps answer the question "What's the best way to get from here to there?" -- at least for computer networks.
Computing Research Highlight of the Week is a service of the Computing Community Consortium and the Computing Research Association designed to highlight some of the exciting and important recent research results in the computing fields. Each week a new highlight is chosen by CRA and CCC staff and volunteers from submissions from the computing community. Want your research featured? Submit it!.




