Project Description: goals and purpose of the project
A content management system is a software system which allows for the organization, control, and publication of a variety of media [3]. Once a submission is entered, an editor reviews it before passing it onto a copyeditor, who finalizes the content. The submission is then laid out, and links or other related media may be added to it. A well-designed content management system automates the workflow while providing a user-friendly interface and security.
The project focused on the content management system of the online magazine at The College of New Jersey, unbound. Based on specifications from Professor Kim Pearson of the journalism program and students in the Interactive Multimedia program, two computer science students working under the direction of Dr. Pulimood had designed and implemented a web-based content management system for Unbound that allows contributors to submit articles with text, images, and audio, from all over the world while protecting information security. The version currently in use provides a complete interface for display of the approved articles. The administrative interface to support the article submission and approval process was minimal and inconsistent with the rest of the website. There were also minimal security features. The aim of this project was to design and implement an administrative user interface consistent with the rest of the website, and following good user interface design principles, as well as to incorporate stringent security checks to maintain privacy and to prevent unauthorized access.
Process used on the project
Work on this project was carried out in four phases background research, design and implementation, testing and analysis, and dissemination. Each student was primarily responsible for her specific area with the weekly meetings providing a forum for dissemination of information and collaborative analysis.
Phase 1: Background Research
Read relevant material to understand the state-of-the-art with respect to content management systems. Did a comparative analysis of current content management systems, especially their features concerning user interfaces and different techniques for secure uploads. Spoke to users of unbound to understand which features they would like to see implemented in their content management system. Researched common web vulnerabilities as well as general security principles.
Phase 2: Design and Implementation
Designed and implemented modules based on the knowledge and insights gained in the previous phase. New interface features include easier navigation through tabbed navigation, more consistent design: both within itself and with web standards, and an enhanced look and feel to the overall interface to create a better experience for the user.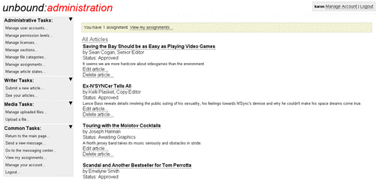
Figure 1. Original unbound interface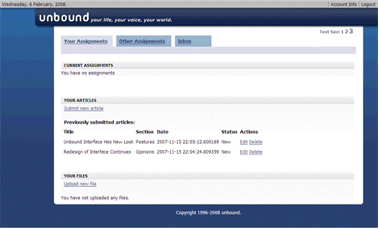
Figure 2. Redesigned interface
Prepare statements have been implemented in order to prevent SQL injection in addition to the current use of a string escape function. A method to regenerate a new session ID if the last session ID is more than thirty seconds old was implemented in order to prevent session hijacking. In addition, a session inactivity time limit of 20 minutes was implemented. The file uploading process has been altered to set a maximum file size and only accept certain types of files. The function htmlentities() was used for some displays of user input in order to prevent cross-site scripting, though not in every instance where database content is displayed, this has been rectified.
Phase 3: Testing and Analysis
Developed performance criteria and test scenarios to be used for testing purposes. Carried out performance and user testing. Analyzed, summarized, and reported results. Identified areas for further improvements and future work. Paros web vulnerability scanner was used to scan both the original unbound admin site as well as the version with the security enhancements in order to compare security improvements.
Phase 4: Dissemination
Presented posters at the ACM Student Research Competition co-located with the 39th SIGCSE Technical Symposium on Computer Science Education (Portland, OR, USA, March 12 - 15, 2008).
References
[1]. Cranor, C.D., Ethington, R., Sehghal, A., Shur, D., Sreenan, C., and van der Merwe, J.E. Design and implementation of a distributed content management system. In Proceedings of the 13th international workshop on Network and operating systems support for digital audio and video (Monterey, CA, 2003). ACM Press, New York, NY, 2003, 4-11.
[2]. Feldstein, Michael. What's important in a learning content management system. In eLearn (Volume 2002 , Issue 5, May 2002). ACM Press, New York, NY, 2002, 4.
[3]. Raskin, Jef. The Humane Interface. Reading, Massachusetts: ACM Press, 2000.
[4]. Simpson, Doug L. Content for one: developing a personal content management system. In Proceedings of the 33rd annual ACM SIGUCCS conference on User services (Monterey, CA, 2005). ACM Press, New York, NY, 2005, 338-342.
[5]. Litwin, P. 2004. Stop SQL Injection Attacks Before They Stop You. MSDN Magazine (Volume 19 Issue 9). Microsoft Corporation.
[6]. Shiflett, C. 2006. Essential PHP Security. O'Reilly Media, Sebastopol, CA.
[7]. Solomon, M.G., and M. Chapple. 2005. Information Security Illuminated. Jones and Bartlett Publishers, Salisbury, MA.
[8]. Sklar, D., and Trachtenberg, A. 2006. PHP Cookbook, 2nd ed. O'Reilly Media, Sebastopol, CA.
[9]. Powers, D. 2006. PHP Solutions: Dynamic Web Design Made Easy. Apress.
[10]. Alshanetsky, I. 2005. Guide to PHP Security, Chapter 3.Marco Tabini & Associates. http://dev.mysql.com/tech-resources/articles/guide-to-php-security.html
[11]. Paros web vulnerability scanner. http://www.parosproxy.org.
[12].. Bueh
rer, G., B.W. Weide, and P.A.G. Sivilotti. 2005. Using parse tree validation to prevent SQL injection attacks. In Proceedings of the 5th international workshop on Software engineering and middleware SEM '05. ACM Press.,
[13]. Su, Z., and G. Wassermann. 2006. The essence of
command injection attacks in web applications. In Conference record of the 33rd ACM SIGPLAN-SIG
ACT symposium on Principles of programming languages POPL '06 (Volume 41 Issue 1). ACM Press.
Conclusions
The unbound content management system is prone to many common web-based system security issues, which have been addressed above. The system now contains several levels of information security against unauthenticated users, injection attacks, cross-site scripting, and other major vulnerabilities described above. Future work on this project should improve user authentication, through tools such as Kerberos, as well as strengthening the system against unaddressed vulnerabilities~Wbrute force attacks and denial of service attacks. In a scan, using the Paros scanner, of the original unbound site, a total of six security vulnerabilities came up, five labeled as "medium risk" and one at "low risk". A scan of the improved security site showed that most of these had been eliminated or reduced most of these. The scanner is limited in its analysis because it does not cover all security vulnerabilities.
The redesign of this user interface provides its users with a simple gateway to perform their work as easily and efficiently as possible. It is suited to their specific needs, and does not contain superfluous features or lack necessary ones. In the long term, it is a vital piece of a content management system which allows for an involved workflow and enables the telling of stories in a more interactive and efficient manner, utilizing key features of the Web. This is beneficial to journalists, making it possible for them to enhance their work without requiring them to learn extensive technology.
Websites Developed and Publications
Web pages developed:
- Karen DelDuca. Designing a User Interface for the Next-Generation Content Management System. ACM Student Research Competition. Finalist. The 39th SIGCSE Technical Symposium on Computer Science Education (Portland, OR, USA, March 12 - 15, 2008). SIGCSE '08. ACM, New York, NY.
- Alexandra Raymond. Information Security for a Web-Based Content Management System. ACM Student Research Competition. The 39th SIGCSE Technical Symposium on Computer Science Education (Portland, OR, USA, March 12 - 15, 2008). SIGCSE '08. ACM, New York, NY.
Back to 2007-2008 Project Listing